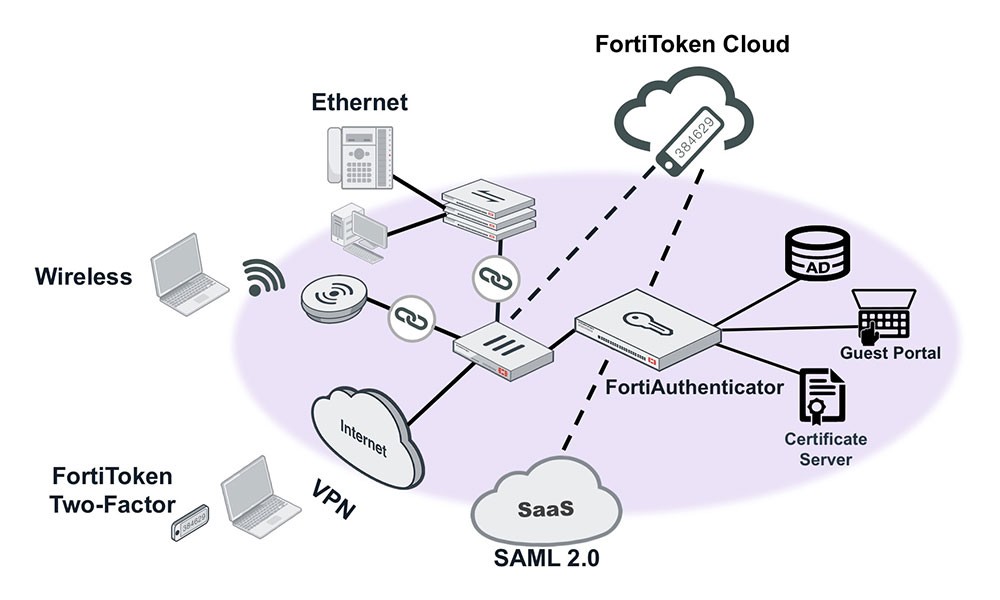
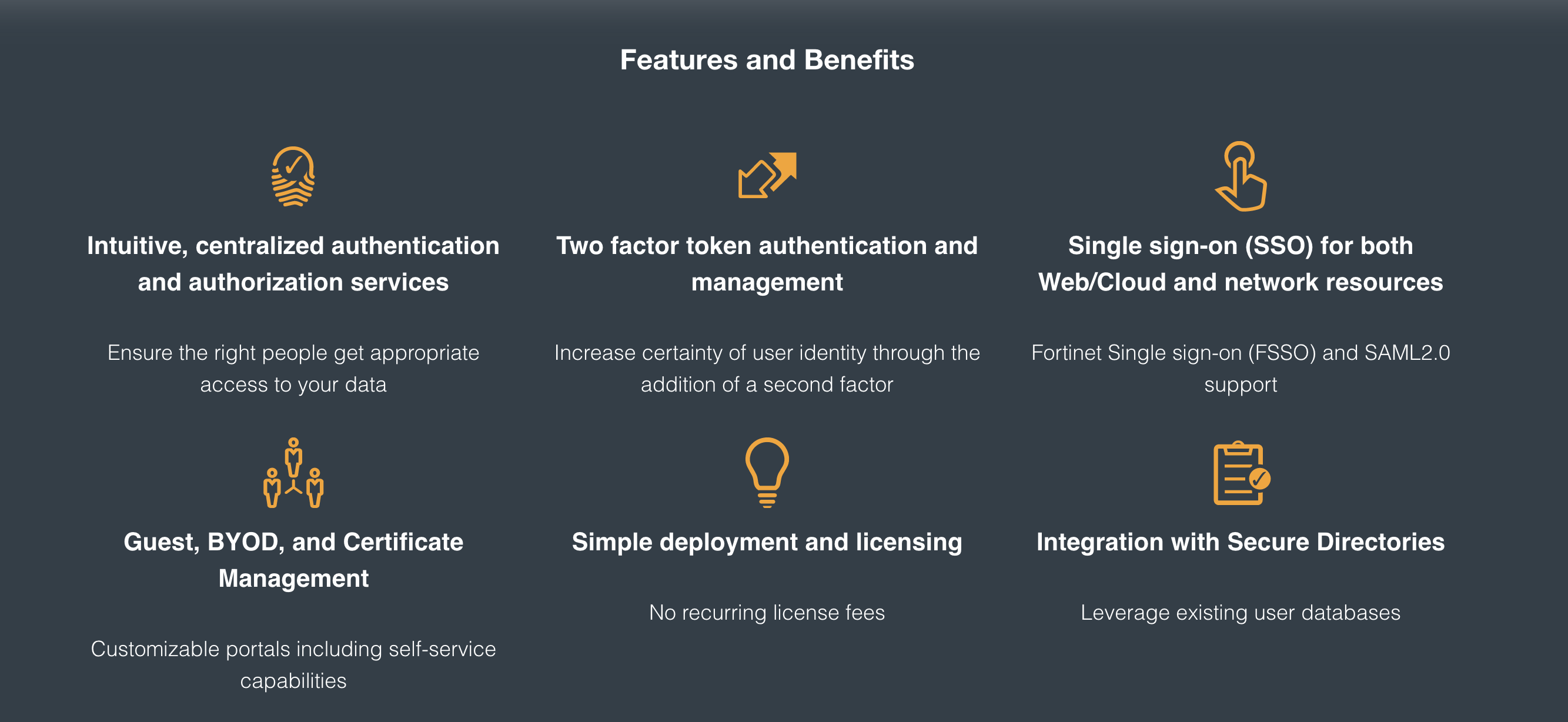
FortiAuthenticator provides centralized authentication services for the Fortinet Security Fabric including single sign on services, certificate management, and guest management.
Hardware Appliances
FAC-200E
Total Users | 500
Description | 4x GE RJ45 ports, 1x 1 TB HDD
FAC-400E
Total Users | 2,000
Description | 4x GE RJ45 ports, 2x 1 TB HDD
FAC-1000D
Total Users | 10,000
Description | 4x GE RJ45 ports, 2x GE SFP, 2x 2 TB HDD
FAC-2000E
Total Users | 20,000
Description | 4x GE RJ45 ports, 2x GE SFP, 2x 2 TB SAS Drive
FAC-3000E
Total Users | 40,000
Description | 4x GE RJ45 ports, 2x GE SFP, 2x 2 TB SAS Drive
FAC-800F
Total Users | 8,000
Description | 4x GE RJ45 ports, 2x GE SFP, 2x 2 TB HDD
Virtual Machines
FAC-VM-Base
Total Users | 100
Description | Base FortiAuthenticator-VM with 100 user license
FAC-VM-100-UG
Total Users | +100
Description | License to add 100 users to base VM
FAC-VM-1000-UG
Total Users | +1000
Description | License to add 1000 users to base VM
FAC-VM-10000-UG
Total Users | +10000
Description | License to add 10000 users to base VM